Search results for Phishing
People
Not Found
Tweets including Phishing
❗WARNING❗
🚨 Top 7702 Delegator Revealed as Phishing Scam 🚨
As thousands rush to enable EIP-7702 smart accounts after Pectra upgrade, dangerous vulnerabilities have emerged. While revolutionary for account abstraction, urgent security risks need attention.
Details ⬇️
Show more
0
0
9
110
16
A few security tips on preventing phishing attacks.
- Never give your password to a "Helpdesk Agent". The real support agents will never need it.
- Don’t click on links you receive in emails. Login to your account only by typing in the URL or through a bookmark. Triple check it’s not a phishing site before entering any password.
- Do NOT use the same password on multiple sites. Use a password manager so that you have a uniquie and strong password for each site. Password managers will also not match on a phishing site domain.
- Use a hardware 2FA like Yubikey. These will prevent most phishing attacks.
Stay SAFU! 🙏
Show more
0
0
156
303
42
Protect your crypto: 5 real phishing attacks, broken down.
Learn how these scams work, and how to avoid them 👉 https://t.co/7kXPaHghyW https://t.co/5BNVegz3AK
0
0
27
80
26
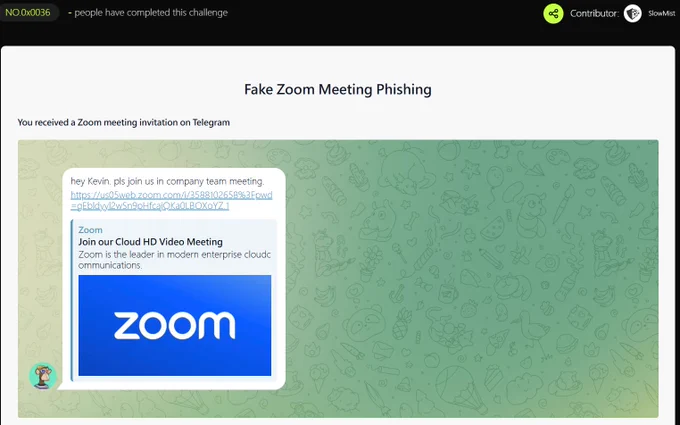
🔥New Unphishable challenge just dropped: Fake Zoom Meeting Phishing.
Job offers turned into attack vectors — a common tactic targeting developers.
Challenge contributor: @SlowMist_Team
If you've been through a similar “recruitment” flow, check your laptop now.
#Unphishable# https://t.co/lfMdujEXyA
Show more
0
0
2
18
8
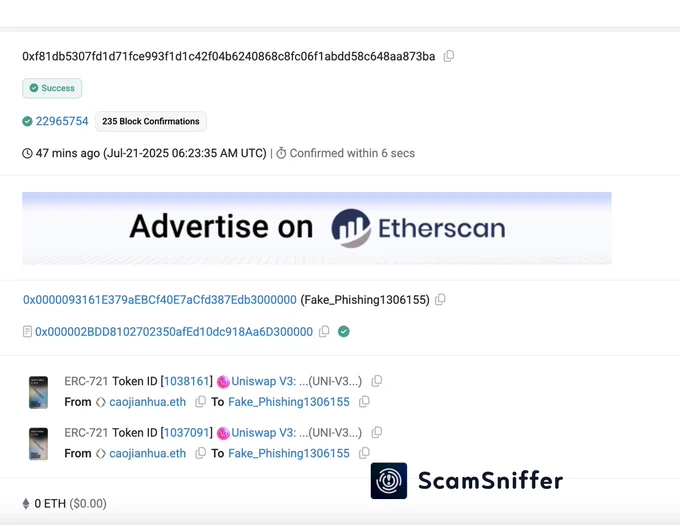
🚨 ALERT: Someone lost $1.23M worth of Uniswap V3 Position NFTs after signing a phishing transaction. 💸 https://t.co/nHcFWMNvdn

0
0
16
94
16
🚨 A fake Ledger scam is making waves again - but it’s not new 🚨
🧵 This phishing dates back to 2021. Victims receive a fake Ledger device in the mail - complete with real-looking packaging and an “official” letter. You’re told to migrate your 24 words from your “old” (real) Ledger to this new (fake) one.
🪤The scam exploits user data from past breaches - name, email and address. You’re told: “Your old device is compromised. Enter your seed phrase into this new secure one.” Once entered - all assets are gone. The fake Ledger is preloaded with malware.
🎭These scams often include:
🔹 Fake user manuals
🔹 Fake “Ledger” software
🔹 Realistic device designs
Some variants even use preset recovery phrases, tricking users into using a wallet the attacker already controls.
📦 Such attacks do work - especially when:
🔹Your order info was leaked
🔹You fall for fake stores or phishing sites selling counterfeit hardware wallets
🔹Your Low awareness around device authenticity checks
🧠These attacks may seem “too physical to scale” - but they don’t need to succeed often. It’s a spray-and-pray model. No confirmed cases of tampering during delivery - but don’t risk it.⚠️
🎯See recap:
🔍 Ledger’s breach:
https://t.co/2XaC94QRV1
🔍 Trezor leak:
https://t.co/djm36qxo5u
🔍 Fake imKey cases:
https://t.co/Y1MVhWcCoT
🔐 How to protect yourself?
✅ Only enter your 24 words on a device you initialized
🚫 Never trust devices from unknown sources
✅ Always verify authenticity via the official brand website
🚫 Don’t fall for unsolicited packages, emails, or “support” messages
📚 Knowledge = prevention.
We maintain a public archive of real-world blockchain hacks, just search by keyword or project name to see if there’s a history of breaches or fraud:
🔎 https://t.co/e90CSvTm6B
🧱 Security starts with verifying the hardware you trust. Stay safe. 🔒 cc @evilcos
Show more
0
0
0
2
2
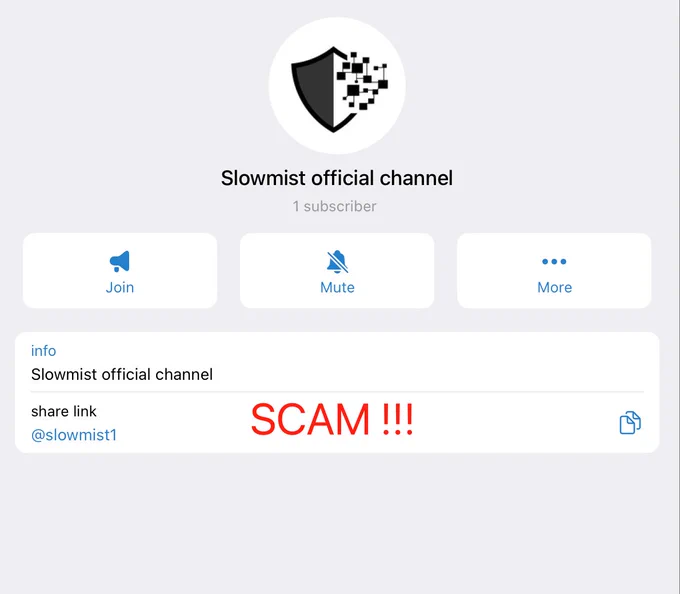
🚨SlowMist Scam Alert🚨
We’ve received reports of fake Telegram groups impersonating #SlowMist# and scamming users via phishing investment links. One example: ❌t[.]me/slowmist1 — this is NOT us.‼️
✅ Please report such groups to Telegram immediately.
For your safety, always refer to our official channels:
1⃣Website: https://t.co/IO2VWk2pae
2⃣X: @SlowMist_Team & @MistTrack_io
3⃣Email: team@slowmist.com
If in doubt, feel free to DM us directly.
⚠️Stay vigilant and verify before you trust.
Show more
0
0
0
4
2
🚨 ALERT: 2 minutes ago, a victim lost $3.13M in WBTC due to signing phishing signatures. https://t.co/rCs4EvT1tN
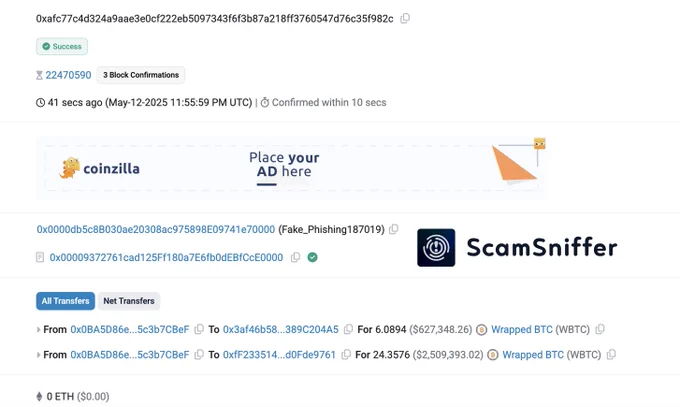
0
0
9
74
19
As things start to get crazy with SOL people will try to take advantage of you more and more so please be careful on chain and remain cautious!
More scams, more hack attempts, more phishing attempts, and more drain attempts you name it it’s going to happen.
I expect things to get crazier so you’ll see everyone come out to take your precious sols.
Show more
0
0
28
52
4
The biggest threat to Web3 isn’t volatility, regulators, or macro. It’s blind signing, phishing, scams, and billions in preventable losses.
We just raised $40M to fix that.
Read the full story → https://t.co/d7nsukWfjk
Show more
0
0
12
107
22
Just got this security warning.
Ledger's Discord admin account was hacked. The scammer falsely claimed a security flaw and urged users to enter their recovery phrases on a phishing site.
Lessons:
1. Never give up your private key recovery phrases no matter who is doing the asking.
2. Social network accounts for a crypto company are often the weakest links.
Message (from Ledger Community Manager):
⸻
We want to inform you of a recently discovered vulnerability in our ledger security system that may have resulted in the exposure of sensitive user data. The potentially affected user data may include:
• Shipping details
• 24-word recovery phrases
• Transaction data linked to recovery phrases Your security is our top priority.
We strongly urge all users to verify the integrity of their recovery phrases by following the steps below:
1. Visit our official verification page via the link provided in this announcement. fakeverify-ledger.appchanged/🔎
2. Connect your wallet by following the on-screen instructions.
3. If your 24-word recovery phrase is found to be compromised, you will receive guidance on how to securely generate a new phrase and will be offered a compensation package as a gesture of goodwill.
Thank you for your attention and cooperation. — The Ledger Team Member
Show more
0
0
138
301
50
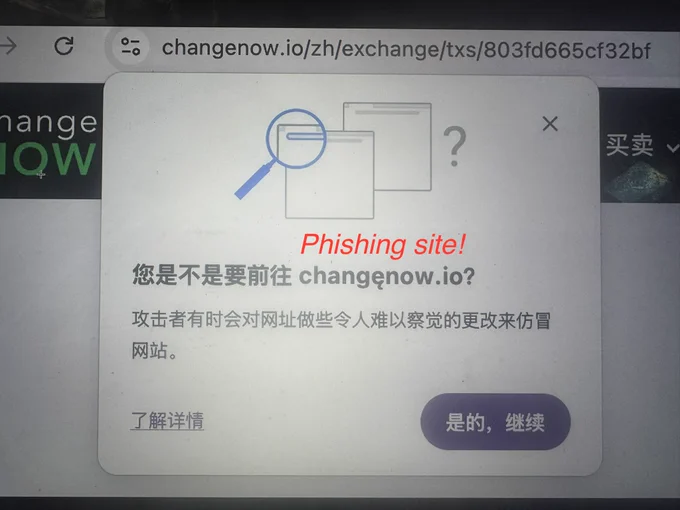
🚨SlowMist Security Alert🚨
A user lost over $20K after visiting a fake @ChangeNOW_io site.
📌Notice the letter “e” in Pic 1?
It’s a #Punycode# attack — a trick we’ve covered in the blockchain dark forest selfguard handbook(Pic 2).
⚠️Beware of browser recommendations — they may suggest phishing sites. Always verify URLs from multiple sources. Here’s a simple way to find the correct official site:
1️⃣ X Verification
Users often rely on the website link shown in a project’s official X account. But don’t trust it blindly — always check the account’s follower count, verification badge, and registration date.⚠️These can be faked. So don’t stop here — proceed to cross-verify.
2️⃣ Cross-Verification
Use trusted platforms like @DefiLlama, @coingecko, or @CoinMarketCap to confirm the domain matches the one on X.
3️⃣ Bookmark It
🛡️For more attack patterns and security tips, check out the blockchain dark forest selfguard handbook:
https://t.co/v6lrUYgrI9
Stay vigilant!
#Phishing# #CryptoSecurity# #Web3#
Show more

0
0
1
4
2
🚨 ALERT: 3 hours ago, a victim lost $859,063 worth of tokens due to signing multiple phishing signatures. https://t.co/SzXTuhPPqx
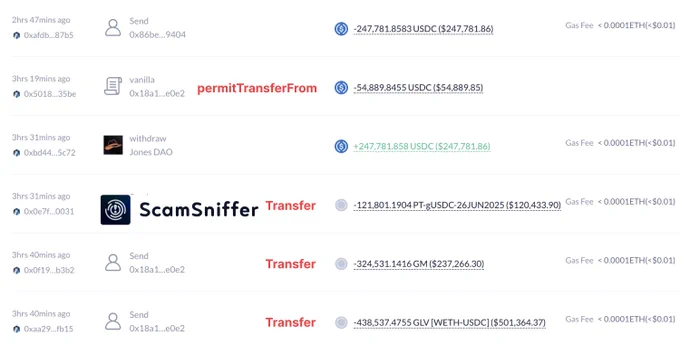
0
0
1
10
3
Most hacks aren’t on-chain. They’re in your habits.
$2.3B lost in 2024. Phishing. Private Key Compromise. Social engineering.
Time to level up your OpSec🫡
Read the full guide & stay Limitless 👇
https://t.co/wF0KOP6rXv
Show more


0
0
7
365
221
🚨 X2Y2 SHUTS DOWN after 3 years of operation! The team is pivoting to an AI-driven crypto project. If you've used X2Y2, make sure to revoke your contract approvals to avoid phishing risks! 🖼
Read more 👉🏼 https://t.co/WvPRnyixBj
Show more


0
0
0
2
0
⚠️ A new malware is targeting crypto wallets, with the goal of stealing funds.
Malware is always evolving. A few ways to remain safe:
✅ Download software only from official sources
✅ Get and use a hardware wallet
✅ Be cautious of phishing links
✅ Enable 2FA where possible
Show more
0
0
53
370
129
🚨 Ethereum's Pectra upgrade (EIP-7702) is live — a major leap forward, but new functionality brings new risks. Here’s what users, wallet providers, developers, and exchanges should watch out for: 🧠
🛡️ For Users:
✅Private key protection should always be a priority.
✅Be aware that the same contract address on different chains may not always have the same contract code.
✅Understand the details of the delegated target before proceeding.
🔍 For Wallet providers:
✅Check if the chain of the delegation matches the current network.
✅Warn users about the risks of delegations signed with a chainID of 0 that could be replayed across different chains.
✅Display the target contract when users sign delegations to reduce the risk of phishing attacks.
🧑💻 For Developers:
✅Ensure permission checks are performed during wallet initialization (e.g., via ecrecover to verify the signing address).
✅Follow the Namespace Formula proposed in ERC-7201 to mitigate storage conflicts.
✅Don't assume that tx.origin will always be an EOA, using msg.sender == tx.origin as a defense against reentrancy attacks will no longer be effective.
✅Ensure that the target contract for the user’s delegation implements the necessary callback functions to ensure compatibility with mainstream tokens.
🏦 For CEXs:
✅Run trace checks on deposits to mitigate the risk of fake deposits from smart contracts.
📚 Full best practices & in-depth analysis:
https://t.co/IvphpT07rA
Show more
0
0
1
10
5










