

SlowMist
@SlowMist_Team
SlowMist is a Blockchain security firm established in 2018, providing services such as security audits, security consultants, red teaming, and more.
404 Following 89.9K Followers
🚨SlowMist TI Alert🚨
MistEye has detected that $sil, created by @AndreCronjeTech four years ago, has been exploited.
As always, stay vigilant!
https://t.co/krApO8HMgs
https://t.co/vvdhpjsZqj https://t.co/omcP4SfyQG
Show more

0
0
2
6
1
🚨SlowMist TI Alert🚨
MistEye has detected potential suspicious activities related to @MiladyStrategy, the root cause is the same vulnerability discovered by @token_works.
As always, stay vigilant!
https://t.co/BGmCIZSSaY https://t.co/bA3OSiWAUC
Show more

0
0
0
2
1
On Sept 13, SlowMist founder @evilcos delivered a 3h lecture at @HKUniversity Business School’s Web3 Global Elite Programme on Blockchain Security.🎓
Topics included:
🔒The “Dark Forest” of #Web3# — threats, trends & case studies
🎣Phishing tactics & defenses
🏦Enterprise-grade solutions for large crypto asset security
🔑Key message: There’s no absolute security in blockchain — only continuous vigilance, verification & systemic defense.
🔗Learn more: https://t.co/SKp3r6Tz9j
Show more


0
0
1
2
1
We’re excited to announce that the Crypto Asset Tracing Handbook is finally here! 🎉
It’s not a dense research paper or a highly technical manual — our goal is to present clear, practical guidance to help more people:
✅Understand the basic framework of on-chain tracing
✅Learn how to use tracing tools
✅Build better judgment & response skills when facing on-chain risks
🤔Many people think:
“Crypto assets are on-chain, every tx is public — recovering funds should be easy, right?”
🙅Not quite. Visibility is only the first step — recoverability is a whole different challenge. Even if you can see the fund flow clearly, you might still have no way to freeze or recover the assets.
That’s why we believe on-chain tracing basics should not be an exclusive skill for security researchers or hackers — it should be essential knowledge for everyone in the crypto ecosystem.
📖GitHub Version:
https://t.co/yizPo1b2Ks
📖PDF Version:
https://t.co/C5E9pCzX0Y
Show more

0
0
4
37
6
🚨SlowMist TI Alert🚨
A community member recently reached out after interviewing with a Web3 team claiming to be from Ukraine. In the first round, he was asked to clone a GitHub repo locally — he wisely refused.🧑💻
🔍Our analysis revealed the repo contains a backdoor: github[.]com/EvaCodes-Community/UltraX
💥If cloned & executed, it would load malicious code, install a malicious dependency rtk-logger@1.11.5 (created 2025-08-08), harvest sensitive browser & wallet data (e.g., Chrome extension storage, possible seed phrases, session tokens) and📤exfiltrate them to the attacker’s server.
⚠️This is a job-offer-as-a-trap scam. Stay vigilant — never run unverified code from unknown sources.
Show more



0
0
1
15
2
🚨SlowMist TI Alert🚨
MistEye detected that @SuperRare has been exploited. The root cause for this exploit was an incorrect permission check in the updateMerkleRoot function, allowing anyone to modify the Merkle Root and claim tokens.
As always, stay vigilant!
https://t.co/ZFoufEcQEH
Show more

0
0
3
30
3
🚨Attackers often distribute malicious files through #LinkedIn#, #Discord#, and #Telegram#.
To stay safe, here are key tips 🛡️:
🔹 Beware of fake jobs asking you to run code from GitHub. Verify identities via official sites.
🔹 Always review unknown code & authors. Use VMs/sandboxes for testing.
🔹 Disable auto-downloads in chat apps. Scan files before opening.
🔹 Enable MFA and regularly update strong, unique passwords
🔗Read more: https://t.co/WOWgbEgeqA
Show more
0
0
0
3
1
🚨 A fake Ledger scam is making waves again - but it’s not new 🚨
🧵 This phishing dates back to 2021. Victims receive a fake Ledger device in the mail - complete with real-looking packaging and an “official” letter. You’re told to migrate your 24 words from your “old” (real) Ledger to this new (fake) one.
🪤The scam exploits user data from past breaches - name, email and address. You’re told: “Your old device is compromised. Enter your seed phrase into this new secure one.” Once entered - all assets are gone. The fake Ledger is preloaded with malware.
🎭These scams often include:
🔹 Fake user manuals
🔹 Fake “Ledger” software
🔹 Realistic device designs
Some variants even use preset recovery phrases, tricking users into using a wallet the attacker already controls.
📦 Such attacks do work - especially when:
🔹Your order info was leaked
🔹You fall for fake stores or phishing sites selling counterfeit hardware wallets
🔹Your Low awareness around device authenticity checks
🧠These attacks may seem “too physical to scale” - but they don’t need to succeed often. It’s a spray-and-pray model. No confirmed cases of tampering during delivery - but don’t risk it.⚠️
🎯See recap:
🔍 Ledger’s breach:
https://t.co/2XaC94QRV1
🔍 Trezor leak:
https://t.co/djm36qxo5u
🔍 Fake imKey cases:
https://t.co/Y1MVhWcCoT
🔐 How to protect yourself?
✅ Only enter your 24 words on a device you initialized
🚫 Never trust devices from unknown sources
✅ Always verify authenticity via the official brand website
🚫 Don’t fall for unsolicited packages, emails, or “support” messages
📚 Knowledge = prevention.
We maintain a public archive of real-world blockchain hacks, just search by keyword or project name to see if there’s a history of breaches or fraud:
🔎 https://t.co/e90CSvTm6B
🧱 Security starts with verifying the hardware you trust. Stay safe. 🔒 cc @evilcos
Show more
0
0
0
2
2
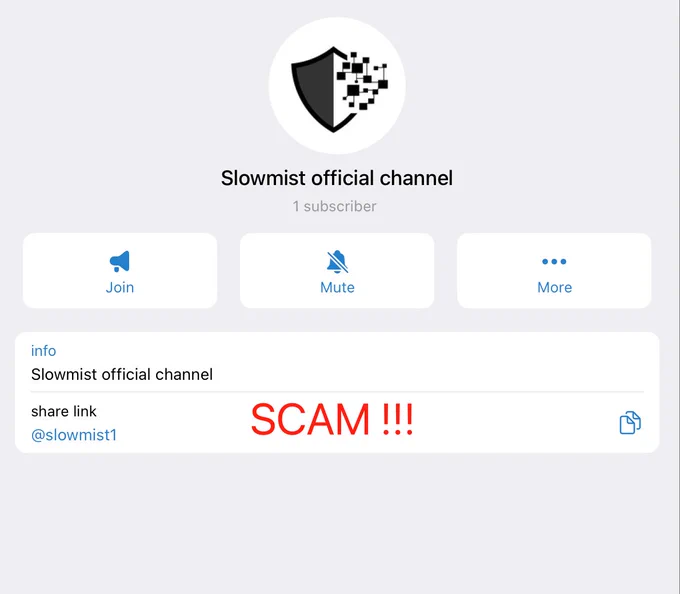
🚨SlowMist Scam Alert🚨
We’ve received reports of fake Telegram groups impersonating #SlowMist# and scamming users via phishing investment links. One example: ❌t[.]me/slowmist1 — this is NOT us.‼️
✅ Please report such groups to Telegram immediately.
For your safety, always refer to our official channels:
1⃣Website: https://t.co/IO2VWk2pae
2⃣X: @SlowMist_Team & @MistTrack_io
3⃣Email: team@slowmist.com
If in doubt, feel free to DM us directly.
⚠️Stay vigilant and verify before you trust.
Show more
0
0
0
4
2
🔥Solana Smart Contract Security Best Practices is back with a major update!🚀
Since its release, the Solana Smart Contract Security Best Practices has received positive feedback from the community, with many developers and security researchers endorsing and recommending the guide.
Based on the latest SlowMist audit experience, we've extensively enhanced the guide to provide comprehensive security solutions for developers within the Solana ecosystem. This update covers vulnerability descriptions, attack scenarios, and fix recommendations.
👀Read the full update on GitHub:
https://t.co/2hVMeo7rHo
#Solana# #SmartContractSecurity# #BlockchainSecurity# #audit#
Show more


0
0
1
12
5
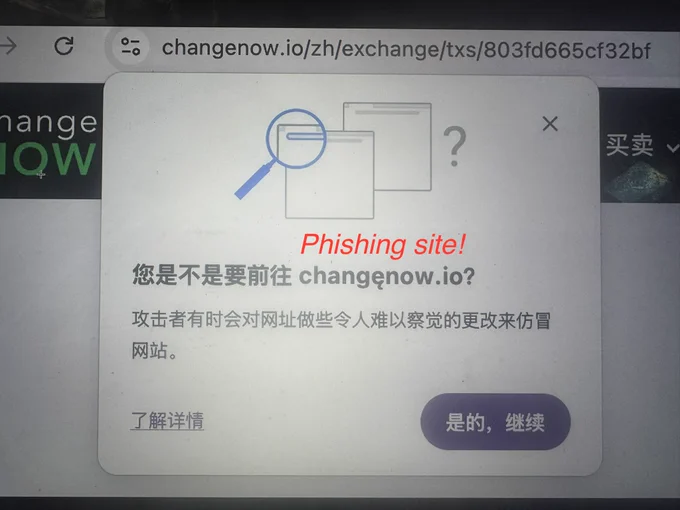
🚨SlowMist Security Alert🚨
A user lost over $20K after visiting a fake @ChangeNOW_io site.
📌Notice the letter “e” in Pic 1?
It’s a #Punycode# attack — a trick we’ve covered in the blockchain dark forest selfguard handbook(Pic 2).
⚠️Beware of browser recommendations — they may suggest phishing sites. Always verify URLs from multiple sources. Here’s a simple way to find the correct official site:
1️⃣ X Verification
Users often rely on the website link shown in a project’s official X account. But don’t trust it blindly — always check the account’s follower count, verification badge, and registration date.⚠️These can be faked. So don’t stop here — proceed to cross-verify.
2️⃣ Cross-Verification
Use trusted platforms like @DefiLlama, @coingecko, or @CoinMarketCap to confirm the domain matches the one on X.
3️⃣ Bookmark It
🛡️For more attack patterns and security tips, check out the blockchain dark forest selfguard handbook:
https://t.co/v6lrUYgrI9
Stay vigilant!
#Phishing# #CryptoSecurity# #Web3#
Show more

0
0
1
4
2
🚨 Ethereum's Pectra upgrade (EIP-7702) is live — a major leap forward, but new functionality brings new risks. Here’s what users, wallet providers, developers, and exchanges should watch out for: 🧠
🛡️ For Users:
✅Private key protection should always be a priority.
✅Be aware that the same contract address on different chains may not always have the same contract code.
✅Understand the details of the delegated target before proceeding.
🔍 For Wallet providers:
✅Check if the chain of the delegation matches the current network.
✅Warn users about the risks of delegations signed with a chainID of 0 that could be replayed across different chains.
✅Display the target contract when users sign delegations to reduce the risk of phishing attacks.
🧑💻 For Developers:
✅Ensure permission checks are performed during wallet initialization (e.g., via ecrecover to verify the signing address).
✅Follow the Namespace Formula proposed in ERC-7201 to mitigate storage conflicts.
✅Don't assume that tx.origin will always be an EOA, using msg.sender == tx.origin as a defense against reentrancy attacks will no longer be effective.
✅Ensure that the target contract for the user’s delegation implements the necessary callback functions to ensure compatibility with mainstream tokens.
🏦 For CEXs:
✅Run trace checks on deposits to mitigate the risk of fake deposits from smart contracts.
📚 Full best practices & in-depth analysis:
https://t.co/IvphpT07rA
Show more
0
0
1
10
5
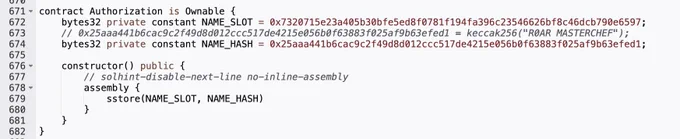
🚨SlowMist Security Alert🚨
The root cause of the @th3r0ar exploit was the presence of a backdoor in the contract
During deployment, the R0ARStaking contract altered the balance (user.amount) of a specified address by directly modifying storage slots. Subsequently, the attacker extracted all funds from the contract through an emergency withdrawal function.
https://t.co/3G0Z1GTjt6
Show more
0
0
0
6
2
🚨SlowMist Security Alert🚨
@zksync security team has identified a compromised admin account that took control of ~$5M worth of ZK tokens — the remaining unclaimed tokens from the ZKsync airdrop.
🧾 Related Address:
0xb1027ed67f89c9f588e097f70807163fec1005d3
As always, stay vigilant!
Show more
0
0
0
4
2
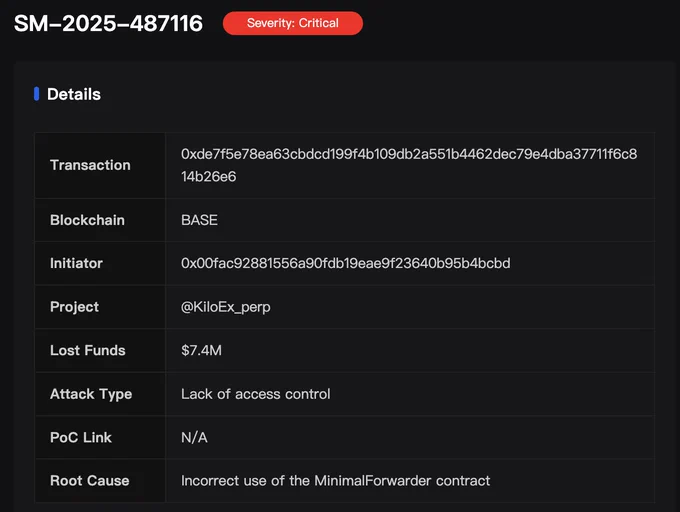
The root cause of the @KiloEx_perp exploit is the lack of access control checks in the top-level contract(MinimalForwarder), which leads to the manipulation of oracle prices.
The attack path is as follows:
1. The setPrices function in the KiloPriceFeed contract, which can modify oracle prices, needs to be called by the Keeper contract.
2. The 0x7a498a61 function in the Keeper contract, which executes price modifications and opening positions, needs to be called by the PositionKeeper contract.
3. The 0xac9fd279 function in the PositionKeeper contract, which executes calls to the Keeper contract, needs to be called by the MinimalForwarder contract.
4. The MinimalForwarder requires users to call the execute function to complete the function call to the PositionKeeper contract. However, within the execute function of the MinimalForwarder contract, users can pass any specified from address and a constructed signature to pass the signature check. Furthermore, there is no check on the data of the external call. This ultimately allows for a step-by-step call to the setPrices function in the KiloPriceFeed contract to tamper with the price.
5. Consequently, the attacker first modified the price to a very low value and used this price to open a long position, then immediately closed the position for profit after adjusting the price to a very high value.
MinimalForwarder:
BASE 0x3274b668aed85479e2a8511e74d7db7240ebe7c8
BSC 0xad37c86c06be706466ee70cbbf58f20655e7efb1
PositionKeeper:
BASE 0xfdc7bc3a9fde88e7bcfb69c8b9ca7fda483627ed
BSC 0xaf457b72fff6712641c5f1843515a6e114b2ecde
Keeper:
BASE 0x796f1793599d7b6aca6a87516546ddf8e5f3aa9d
BSC 0x298e94d5494e7c461a05903dcf41910e0125d019
KiloPriceFeed:
BASE 0x22c40b883b5976f13c78ee45ead6b0cdc192dae5
BSC 0x1b64eb04f9e62e1f3d1599d65fcfa8cc2dc44024
As always, stay vigilant!
Show more
0
0
0
10
6














