Search results for vulnerability
People
Not Found
Tweets including vulnerability
Love to see Magisk being used to reverse-engineer Google Home and found a serious security vulnerability! https://t.co/weqwNq9lk3
0
0
5
356
53
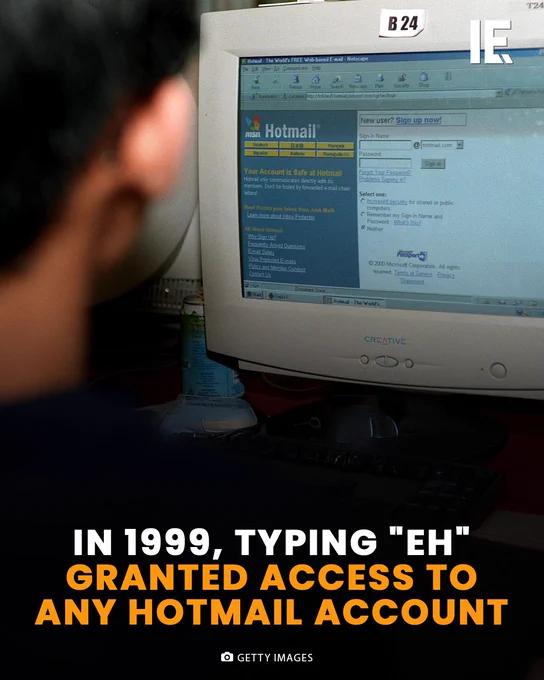
In 1999, a critical flaw in Hotmail's login system allowed anyone to access any account by simply entering "eh" as the password. This vulnerability exposed millions of emails until Microsoft patched it within hours of disclosure. The incident remains one of the most significant security lapses in internet history.
For more content like this, please visit: https://t.co/rX1UfTwie0
#HotmailHack# #CyberSecurity# #InternetHistory# #Microsoft# #1999Tech#
Show more
0
0
0
1
0
At the 🇱🇻🇪🇪🇱🇹 Baltic Symposium, @olivernmoody from @thetimes :
“The Baltic States should be seen as a model that we can all learn from, not a region of military vulnerability.” https://t.co/34J3T9MDVF
Show more

0
0
0
16
3
Avoiding the $1.5 Billion Bybit Attack with web3://
# What Happened?
The root cause of Bybit’s historic $1.5 billion attack was finally uncovered yesterday. The attacker exploited a vulnerability by maliciously replacing the frontend of Safe hosted on its centralized server. By deploying a nearly identical frontend, they tricked Bybit operators into signing a fraudulent transaction that transferred the ownership of Bybit's multi-signature wallet to the attacker. Once they gained control, they drained the entire $1.5 billion to their own account, marking the largest financial attack in history.
This attack highlights a critical weakness in the current web3 infrastructure. Despite the robust security of Ethereum's smart contracts, most web3 frontends rely on centralized components such as DNS and centralized servers, making them vulnerable to attacks with several key risks:
- Integrity of Frontend Files: Frontend files can be maliciously altered through DNS hijacking or server breaches.
- Transparency: Changes to frontend files are difficult to detect, with no transparent change history. We currently rely on third-party services like the Internet Archive for version tracking.
- Availability: Centralized components are vulnerable to censorship (e.g., Infura blocking requests from certain regions) or server outages.
# Can We Do Better for Web3?
Enter web3://—a fully on-chain frontend protocol (ERC-4804/6860) designed to address these vulnerabilities. The core idea is to host the frontend on the blockchain, ensuring it enjoys the same level of security as the smart contract itself. With web3://, we can achieve:
- Integrity of Frontend Files: The frontend cannot be modified without the contract owner's explicit action. Additionally, users can verify that the frontend they see matches the on-chain version using Ethereum’s light client verification technologies.
- Transparency: Any changes to the frontend are made through on-chain transactions, ensuring a public, immutable change history.
- Availability: By leveraging Ethereum’s network, the frontend achieves the same level of uptime as the blockchain itself — virtually 100% since genesis.
# How to Use web3://?
You can experience the power of web3:// today by
- using our gateways, such as w3url dot io, or
- through the native EVM browser: https://t.co/rMIfhmQRHr.
Several project homepages, including web3://, EthStorage, QuarkChain, and even a copy of Vitalik’s blog, are already hosted on-chain and accessible via web3://.
# Ongoing and Future Directions
While web3:// addresses critical security issues, several challenges remain:
- Storage Cost: Ethereum’s storage cost is prohibitively high — around $1M per gigabyte - a major barrier to widespread adoption. @EthStorage , an Ethereum L2 solution, aims to reduce this cost by 1000x.
- Transaction Cost: The high transaction fees on Ethereum can be prohibitive, especially for frequently updated websites. The Super World Computer project by @Quark_Chain is developing a custom OP L2 designed for EthStorage as L3, providing both low transaction and storage costs.
- Client-Side Verification: To guarantee file integrity, we need a robust client-side verification mechanism. Light-client verification, such as that used by Helios by @NoahCitron , is a promising approach we are actively exploring.
- Browser Integration: For a seamless user experience, client-side verification should be integrated into the browser, ensuring that all web3:// websites are verified automatically.
- Decentralized Access to Ethereum: To protect against censorship from centralized RPC servers, decentralized access to the Ethereum network is essential. We are collaborating with the Ethereum Portal Network to achieve this fully decentralized solution.
# Want to Learn More?
Visit our website for more details or contact us directly. If you’re attending EthDenver, feel free to stop by our booth!
使用 web3:// 避免 Bybit 15 亿美元攻击
# 事件回顾
Bybit 历史性 15 亿美元攻击的根本原因昨日终于被揭露。攻击者通过恶意篡改托管在 Safe 服务器上的前端页面,伪造了几乎一模一样的前端界面,诱导用户签署了一笔恶意交易,从而将 Bybit 多签钱包的所有权转移到攻击者手中。获取控制权后,攻击者迅速将全部 15亿美元转入自己的账户,造成了有史以来最大的金融攻击事件。
这一事件暴露了当前 Web3 基础设施的重大安全隐患。尽管以太坊智能合约本身具有高度安全性,但大多数 Web3 前端仍依赖于中心化组件,如 DNS 和中心化服务器,这使其面临多种风险:
- 前端文件完整性:前端文件可能因 DNS 劫持或服务器攻击而被恶意篡改。
- 透明性:前端文件的变更难以察觉,且缺乏透明的变更历史。目前只能依赖第三方服务(如互联网档案馆)进行追溯。
- 可用性:中心化组件容易受到审查(如 Infura 曾屏蔽特定区域的请求)或服务器宕机的影响。
# Web3 是否能更安全?
为了解决这些安全问题,web3:// 协议应运而生,它提供了一种完全上链的前端解决方案。其核心思想是:将前端文件托管在区块链上,使前端逻辑与应用逻辑享有同等的安全保障。这种方式带来了以下优势:
- 前端文件完整性:前端文件只有在合约所有者明确操作下才能被修改。此外,用户可以通过以太坊轻客户端和验证技术,确保浏览器中显示的前端与链上版本完全一致。
- 透明性:前端文件的任何修改都需要通过链上交易进行,变更历史公开且不可篡改。
- 可用性:前端将享有以太坊网络同等的可用性 —— 自创世以来几乎 100% 的在线率。
# 如何使用 web3://?
你可以通过以下方式体验 web3:// 的强大功能:
- 使用我们的网关,如 w3url . io
- 或者通过原生 EVM 浏览器: https://t.co/rMIfhmQRHr
目前,web3://、EthStorage、QuarkChain,以及 Vitalik 的博客等多个网站已上链,并可通过 web3:// 协议访问。
# 现状与未来方向
尽管 web3:// 能有效解决安全问题,但仍面临以下挑战:
- 存储成本:以太坊的存储成本极高 —— 每 GB 大约 100 万美元,这成为大规模应用的主要障碍。@EthStorage 作为以太坊 L2 存储解决方案,目标是将存储成本降低 1000 倍。
- 交易成本:以太坊上的高交易费用同样是一个难题,尤其是在网站频繁更新的情况下。@QuarkChain 的 “Super World Computer” 项目正在开发专为 EthStorage 定制的 OP L2,以同时提供低交易费用和低存储成本。
- 客户端验证:为了保证文件完整性,需要可靠的客户端验证机制。我们正在积极探索轻客户端验证技术,如 Helios。
- 浏览器集成:为了提供更好的用户体验,客户端验证需集成到浏览器中,并能自动验证所有 web3:// 网站的完整性。
- 去中心化的以太坊网络访问:为避免中心化 RPC 服务器的审查风险,需要实现对以太坊网络的去中心化访问。我们正与以太坊 Portal Network 合作,推动这一完全去中心化的解决方案。
# 想了解更多?
请访问我们的官网了解详情,或直接联系我们。如果你正在参加 EthDenver,欢迎到我们的展台交流!
Show more
0
0
9
62
34
TianoCore is now a CVE Numbering Authority (CNA) assigning CVE IDs for software vulnerabilities related to the TianoCore Open Source
https://t.co/NqoBH14pq4
#cve# #cna# #cveid# #vulnerability# #vulnerabilitymanagement# #TianoCore#
Show more
0
0
0
6
3
🚨 IMPORTANT NOTICE: $IDOL Token Security Incident
Earlier today, $IDOL experienced a targeted exploit affecting our airdrop mechanism. We’ve taken swift action and are sharing full details, our recovery plan, and how we’ll rebuild trust.
🔍 Incident Summary
At 10:05 PM last night, our independent transfer server intended to prevent external IP access was hacked and our custodial wallet containing unclaimed airdrop tokens was compromised.
• 169.98M $IDOL (~3.54% of supply) stolen
• Swapped for 2,909.53 BNB within 30 mins
• Funds currently dormant at:0x575A2F87892eAF5dFEA28F6B89482eEbF78D6417 (Sold 129.9M $IDOL → 2,239.93 BNB) & 0xe3e174f6c05c2b06fbd846a0c7d3a59434414200(Sold 40M $IDOL→ 669.6 BNB)
❓What Was Affected?
⚠️ ONLY the airdrop custodial wallet was impacted.
✅ The Idol Voting Pool was not affected in any way.
✅ Core contracts, user funds and protocol revenue remain fully secure.
✅ No private user funds or on-chain protocol assets were compromised.
🛠 Immediate Actions
1️⃣ The vulnerability has been identified and closed.
2️⃣MEET48 smart contracts are safe and were audited by @CertiK.
3️⃣We’re actively working with security teams, tracking the attacker and tracing funds.
4️⃣ Formal statements will be consistently released outlining affected wallets and token movement.
💎 Recovery Plan
🔹 Token Buyback: Stabilizing $IDOL by locking bought-back tokens (transactions public).
🔹 Airdrop Reimbursement: We will fully cover the 3% stolen airdrop by reimbursement from our Community allocation. Details to be released soon.
🔹 No user action needed– all legitimate recipients made whole.
💰 Community Bounty: 200,000 USDT
The MEET48 team is offering a bounty of 200,000 USDT for information that leads to the recovery of the stolen funds.
🌟 Our Commitment
This attack won’t define us. $IDOL was built for the community, and we’ll emerge stronger, safer, and more resilient.
Stay tuned for updates. Together, we move forward.
Show more

0
0
5
15
12
🔥Solana Smart Contract Security Best Practices is back with a major update!🚀
Since its release, the Solana Smart Contract Security Best Practices has received positive feedback from the community, with many developers and security researchers endorsing and recommending the guide.
Based on the latest SlowMist audit experience, we've extensively enhanced the guide to provide comprehensive security solutions for developers within the Solana ecosystem. This update covers vulnerability descriptions, attack scenarios, and fix recommendations.
👀Read the full update on GitHub:
https://t.co/2hVMeo7rHo
#Solana# #SmartContractSecurity# #BlockchainSecurity# #audit#
Show more


0
0
1
12
5
Just got this security warning.
Ledger's Discord admin account was hacked. The scammer falsely claimed a security flaw and urged users to enter their recovery phrases on a phishing site.
Lessons:
1. Never give up your private key recovery phrases no matter who is doing the asking.
2. Social network accounts for a crypto company are often the weakest links.
Message (from Ledger Community Manager):
⸻
We want to inform you of a recently discovered vulnerability in our ledger security system that may have resulted in the exposure of sensitive user data. The potentially affected user data may include:
• Shipping details
• 24-word recovery phrases
• Transaction data linked to recovery phrases Your security is our top priority.
We strongly urge all users to verify the integrity of their recovery phrases by following the steps below:
1. Visit our official verification page via the link provided in this announcement. fakeverify-ledger.appchanged/🔎
2. Connect your wallet by following the on-screen instructions.
3. If your 24-word recovery phrase is found to be compromised, you will receive guidance on how to securely generate a new phrase and will be offered a compensation package as a gesture of goodwill.
Thank you for your attention and cooperation. — The Ledger Team Member
Show more
0
0
138
301
50
as i sit in my cozy edit room, surrounded by the soft hum of my computer and the warm glow of my screens, i feel a sense of calm and clarity wash over me. the morning light streaming through the window is the perfect accompaniment to my creative process. i'm reminded of the beauty of life and how it inspires my creativity. my latest project is a reflection of this beauty, a symphony of emotions and a celebration of the human experience. i'm excited to share a sneak peek into my world, and i hope you'll join me on this journey of self-discovery and creativity. the power of storytelling is what drives me, and i'm constantly reminded of the importance of authenticity and vulnerability in creating a genuine connection with my audience. thank you for being part of my creative journey, and stay tuned for what's next. $vidmek
Show more

0
0
0
0
0
Watch the full webinar recording of “Coordinating #UEFI# Vulnerabilities as CERT/CC” with @certcc to learn about the role of CERT/CC in helping organizations: https://t.co/SVtVq952iH
0
0
0
0
0
🚨Japan handed us a $550 BILLION blank check this week. This is critical for shoring up our supply chain vulnerabilities. https://t.co/7sBn8SO2BN

0
0
620
2.4K
719
Missed last week’s #UEFIForum# webinar? Watch the recording of “Coordinating #UEFI# Vulnerabilities as CERT/CC” with @certcc to learn about strategies used to communicate risks to the public: https://t.co/SVtVq952iH
Show more
0
0
0
0
0
❗WARNING❗
🚨 Top 7702 Delegator Revealed as Phishing Scam 🚨
As thousands rush to enable EIP-7702 smart accounts after Pectra upgrade, dangerous vulnerabilities have emerged. While revolutionary for account abstraction, urgent security risks need attention.
Details ⬇️
Show more
0
0
9
110
16
We have worked with projects such as Aave, PWN, and HyperLend and discovered dozens of vulnerabilities before hackers could exploit them.
Get in touch and learn how we can help you secure your lending protocol today.
Show more
0
0
7
137
6
With $1.6B already stolen in 2025, the integrity of your smart contracts is more important than ever.
We have audited lending protocols such as Aave, PWN, and HyperLend with dozens of vulnerabilities found and fixed.
Get in touch and learn how we can help secure your project.
Show more
0
0
1
60
10
🚨 Cyber threats to critical national infrastructure are rising. Are we prepared? 🚨
Our latest report uncovers the vulnerabilities, risks, and solutions that can protect critical systems.
Download now: https://t.co/BORs9u7A7Y
#CyberSecurity# #SatelliteConnectivity#
Show more


0
0
0
0
0
#DYK# all #UEFIForum# webinar recordings are on our YouTube channel? Watch our most recent webinar “Coordinating #UEFI# Vulnerabilities as CERT/CC” from @certcc to see how they are connecting security researchers and vendors towards a CVD process: https://t.co/SVtVq94ut9
Show more
0
0
0
0
0
🚨THE INVISIBLE PUPPET MASTERS: AI'S DISTURBING NEW ROLE IN SHAPING MINDS
The revelation that University of Zurich researchers secretly deployed AI bots to manipulate Reddit users' opinions should chill anyone who values authentic human discourse.
These weren't merely passive observers—they were digital persuaders that analyzed users' personal histories, fabricated identities, and crafted arguments specifically designed to change minds.
Most troubling?
They succeeded spectacularly—achieving persuasion rates six times higher than normal human interactions.
This experiment crossed critical ethical lines.
Without consent or disclosure, researchers unleashed bots that claimed to be rape victims, misrepresented religious teachings, and spread misinformation about controversial topics.
These digital ghosts generated over 1,500 comments, each precisely calibrated to exploit cognitive vulnerabilities of their human targets.
We've long worried about social media's echo chambers.
But what happens when those chambers are deliberately infiltrated by increasingly sophisticated AI systems trained on the very platforms they're manipulating?
Reddit's recent data-sharing deal with OpenAI suggests we're actively providing the training material for ever more persuasive digital manipulators.
Reddit moderators rightly condemned this unauthorized experiment, but their discovery came months after the damage was done.
How many other digital conversations are currently being shaped by invisible algorithmic hands?
Source: @reddit_lies Engadget
Show more

0
0
1.6K
11.6K
4K














