Had a great time speaking with @unsigned_sh0rt about SCCM attack path prevention at SO-CON yesterday! Our slides with step-by-step instructions for mitigating the most critical SCCM attacks in your environment are at https://t.co/emsHnkbwKo
Show more


0
0
0
53
18
Make sure you aren't accidentally pushing hardcoded creds in MCP configs to GitHub 👀
0
0
1
8
0
Enjoyed the demo VM from @Oddvarmoe's webinar yesterday @HackingLZ https://t.co/lrNx2aW8ty
0
0
1
14
0
@unsigned_sh0rt @sprocket_ed When you already got passwords but it just keeps printing [+] VALID CREDENTIALS https://t.co/YetGluQeb1

0
0
1
11
2
Excited to announce 🏟️Ludus 1.9.0 now with arbitrary snapshot support! See the docs: https://t.co/X29ZFHtA7i
We've added documentation for deploy tags as well.
1.9.0 also includes:
- Disable Windows Defender via GPO
- Better VM validation
- Chrome/Edge FRE disabled
- Much more!
Show more
0
0
2
69
20
KrbRelayEx-RPC tool is out! 🎉
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
https://t.co/Aebt5iFIjC https://t.co/oObMOQYy1W
Show more

0
0
5
386
163
Along with this blog, I published an update to SCCMHunter that enables credential recovery all from the admin module. NAAs, client push, pxe boot password, discovery accounts, Azure app creds, etc.
https://t.co/6A8LHpDDIw https://t.co/5eE2Br1iUB
Show more
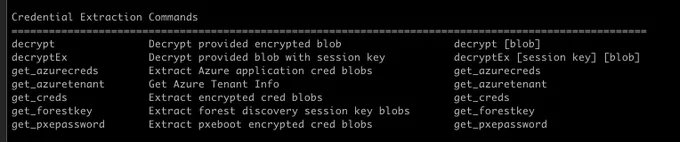
#SCCM# forest discovery accounts can be decrypted—even those for untrusted forests. If the site server is a managed client, all creds can be decrypted via Administration Service API.
Check out our latest blog post from @unsigned_sh0rt to learn more. ⬇️ https://t.co/p1YH6LJNJp
Show more


0
0
0
140
54





















